After nearly a year, President Obama’s administration released the final version of their National Strategy for Trusted Identities in Cyberspace (NSTIC), on April 15th. The full NSTIC strategy document can be found here.
The NSTIC strategy lays out a roadmap for the public and private sectors to build an “ecosystem”, whereby identities of individuals, networks, services and devices involved in online transactions can be trusted, according to the final document. “The old password and username combination we often use to verify people is no longer good enough,” said Commerce Secretary Gary Locke, during Friday’s unveiling of the strategy at the U.S. Chamber of Commerce. “It leaves too many consumers, government agencies and businesses vulnerable to identity and data theft.”
A recent Federal Bureau of Investigation report stated that “identity theft has emerged as a dominant and pervasive financial crime that exposes individuals and businesses to significant losses and undermines the credibility and operation of the entire U.S. financial system.”
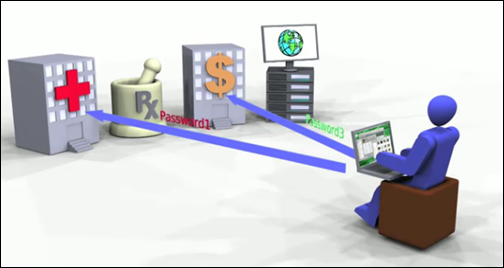
A contributing factor is the unmanageable number of passwords people must remember to access their online accounts. Many people don’t even try; they just re-use the same ones for all of their accounts, making it that much easier for identity thieves.
The National Strategy for Trusted Identities in Cyberspace (NSTIC) envisions a cyber world – the Identity Ecosystem – that improves upon the passwords currently used to log-in online. It would include a vibrant marketplace that allows people to choose among multiple identity providers – both private and public – that would issue trusted credentials that prove identity.
- Faster: Once you use your credential to start an online session, you would not need to use separate usernames and passwords for each Web site. For example, your computer or cell phone could offer your “trusted ID” to each new site where you want to use the credential. The system would work much like your ATM card works now. By having the card and a pin number you can use your ATM card all over the world. By having a credential and a password you would be able to use you trusted ID at many different sites. This saves you time while enhancing security. No more searching in your drawer for your list of passwords.
- More convenient: Businesses and the government will be able to put services online that have to be conducted in person today like transferring auto titles or signing mortgage documents.
- Safer: Your trust credential will foil most commonly used attacks from hackers and criminals, protecting you against theft and fraud, safeguarding your personal information from cyber criminals.
- Private: This new “identity ecosystem” protects your privacy. Credentials share only the amount of personal information necessary for the transaction. You control what personal information is released, and can ensure that your data is not centralized among service providers.
- Voluntary: The identity ecosystem is voluntary. You will still be able to surf the Web, write a blog, participate in an online discussion, and post comments to a wiki anonymously or using a pseudonym. You would choose when to use your trusted ID. When you want stronger identity protection, you use your credential, enabling higher levels of trust and security.
The strategy has received widespread support from private sector companies, such as PayPal, Microsoft and Adobe; advocacy and academic organizations, such as the Center for Democracy and Technology, and the American Bar Association; as well as members of Congress…more





